[Task 1] Intro
[Task 2] Methodology
[Task 3] [Section 1: SSH] — Intro
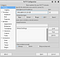
[Task 4] [Section 1: SSH] — Putty and ssh
- Download Putty here:
https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
Or using linux
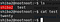
apt install putty2. Login using Putty
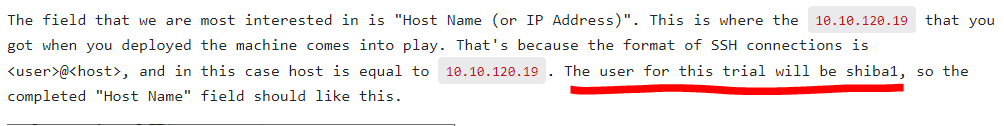
username: shiba1Enter username, ip and click Open
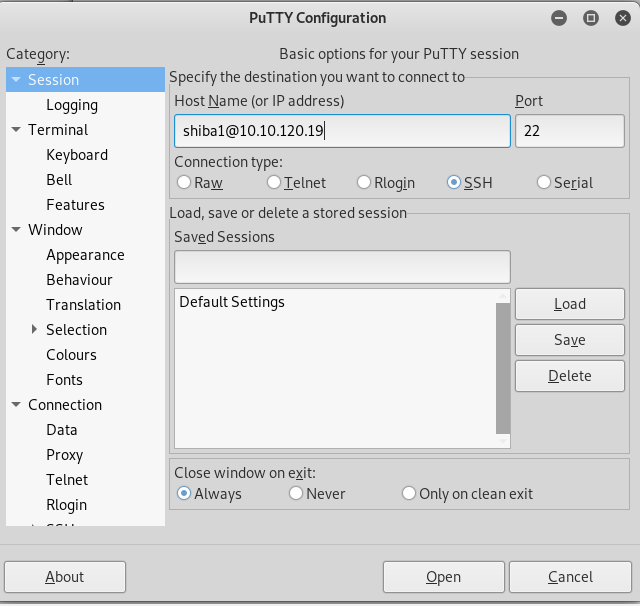
Click Accept
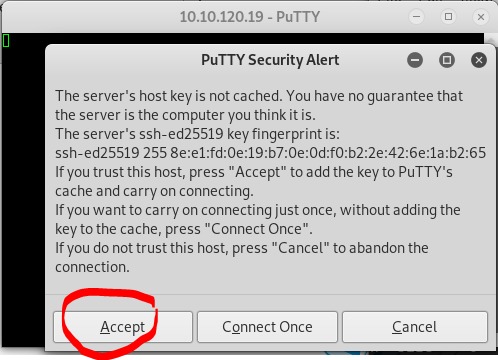
Enter password “shiba1”
3. Login using command line in linux or windows
ssh <username>@<ip>[Task 5] [Section 2: Running Commands] — Basic Command Execution
echo hello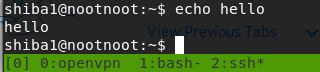
[Task 6] [Section 2: Running Commands] — Manual Pages and Flags
- How would you output hello without a newline
man echo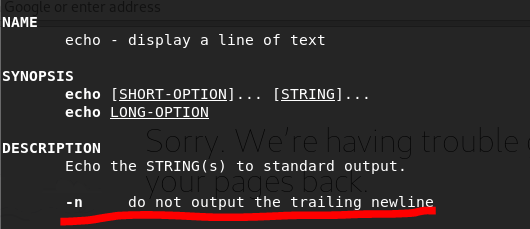
echo -n hello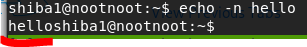
[Task 7] [Section 3: Basic File Operations] — ls
- What flag outputs all entries
ls -a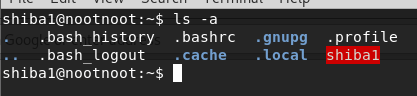
2. What flag outputs things in a “long list” format
ls -l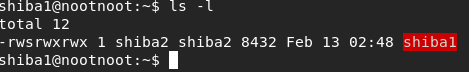
[Task 8] [Section 3: Basic File Operations] — cat
- What flag numbers all output lines?
cat --help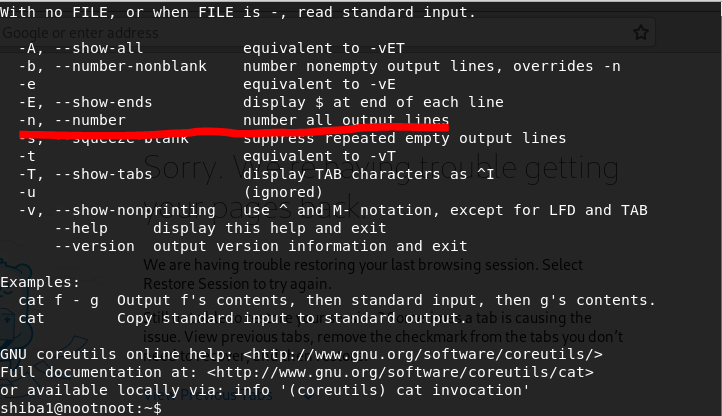
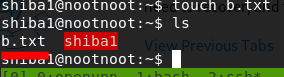
[Task 9] [Section 3: Basic File Operations] — touch
touch b.txtls
[Task 10] [Section 3: Basic File Operations] — Running A Binary
- How would you run a binary called hello using the directory shortcut . ?
./hello2. How would you run a binary called hello in your home directory using the shortcut ~ ?
~/hello3. How would you run a binary called hello in the previous directory using the shortcut .. ?
../hello[Task 11] Binary — Shiba1
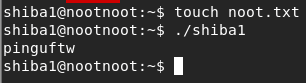
- What’s the password for shiba2
touch noot.txt./shiba1
[Task 12] su
- How do you specify which shell is used when you login?
su --help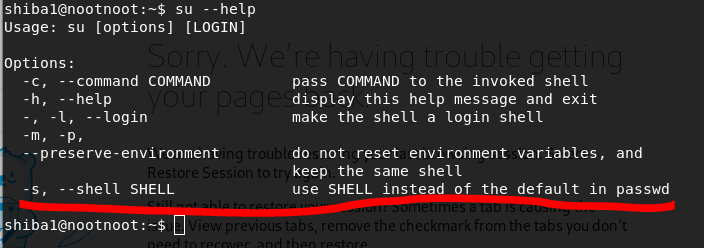
[Task 13] [Section 4 — Linux Operators]: Intro
su shiba2[Task 14] [Section 4: Linux Operators]: “>”
- How would you output twenty to a file called test
echo twenty > test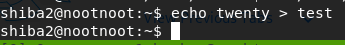
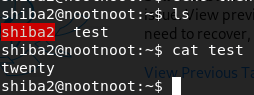
ls cat test
[Task 15] [Section 4: Linux Operators]: “>>”
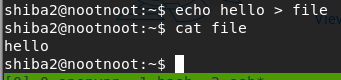
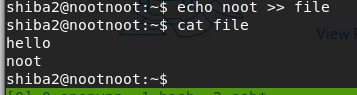
echo hello > filecat file
echo noot >> filecat file
[Task 16] [Section 4: Linux Operators]: “&&”
echo hello >> file2 && cat file2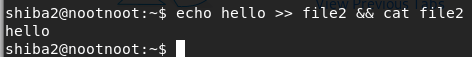
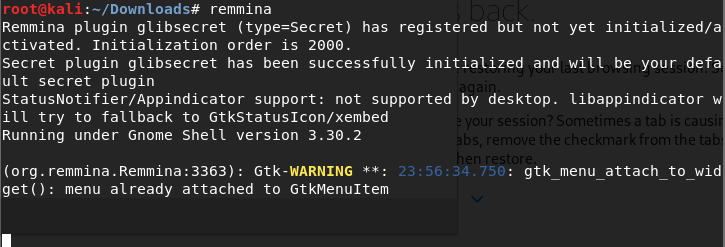
[Task 17] [Section 4: Linux Operators]: “&”
Let’s open GUI app on my machine
try without “&”
Press “Enter”, You can see that you can not type any command.
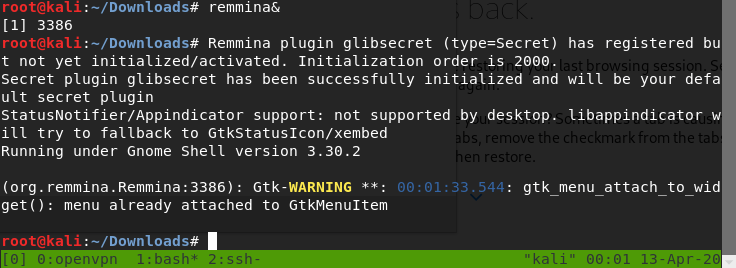
try with “&” and Press “Enter”. You can type any command after it.
[Task 18] [Section 4: Linux Operators]: “$”
echo $USER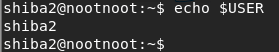
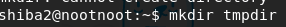
mkdir tmpdircd tmpdirtouch $USERls
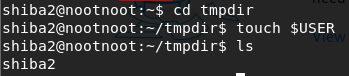
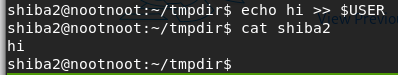
touch $USERecho hi >> $USERcat shiba2
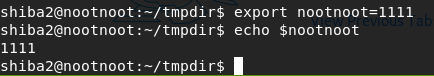
- How would you set nootnoot equal to 1111
export nootnoot=1111echo $nootnoot
2. What is the value of the home environment variable
echo $HOME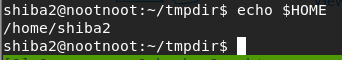
[Task 19] [Section 4: Linux Operators]: “|”
Let’s try with “passwd”
cat /etc/passwdThere’re string “noot”
Let’s try with “|”
cat /etc/passwd | grep noot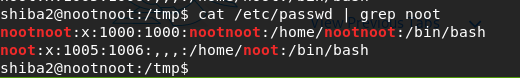
[Task 20] [Section 4: Linux Operators] — “;”
sdasdasdsa; ls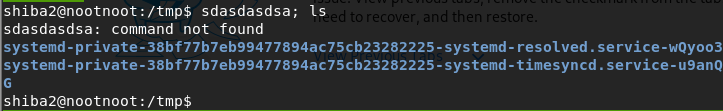
[Task 21] Binary — shiba2
- What is shiba3’s password
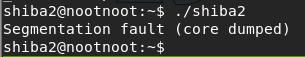
Let’s run “shiba2” first.
./shiba2Error!!!
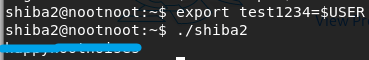
Export variable “test1234”
export test1234=$USER./shiba2
[Task 22] [Section 5 — Advanced File Operations]: Intro
su shiba3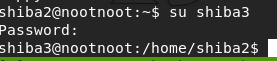
[Task 23] [Section 5 — Advanced File Operators]: A bit of background.
[Task 24] [Section 5: Advanced File Operations]: chmod
[Task 25] [Section 5: Advanced File Operations] — chown
- How would you change the owner of file to paradox
ANS: chown <owner> file - What about the owner and the group of file to paradox
ANS: chown <owner>:<group> file - What flag allows you to operate on every file in the directory at once?
ANS: -r
[Task 26] [Section 5: Advanced File Operations] — rm
rm --help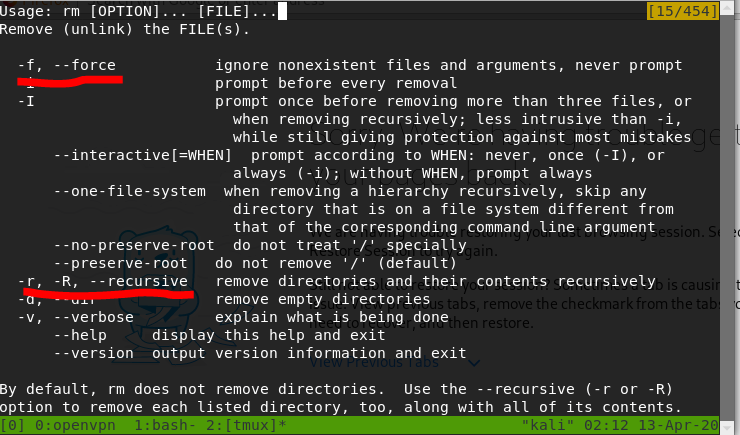
[Task 27] [Section 5: Advanced File Operations] — mv
- How would you move file to /tmp
ANS: mv file ****
[Task 28] [Section 5: Advanced File Operations] — cp
echo test > testfilecp testfile testfile2
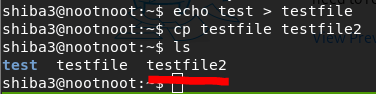
[Task 29] [Section 5: Advanced file Operations] — cd && mkdir
- Using relative paths, how would you cd to your home directory.
ANS: cd ~ - Using absolute paths how would you make a directory called test in /tmp
ANS: mkdir /tmp/test
[Task 30] [Section 5: Advanced File Operations] ln
Let’s try the command
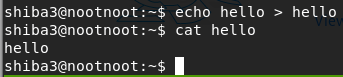
echo hello > hellocat hello
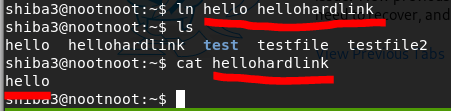
ln hello hellohardlinklscat hellohardlink
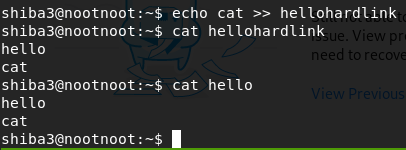
echo cat >> hellohardlinkcat hellohardlinkcat hello
- How would I link /home/test/testfile to /tmp/test
ANS: ln /home/test/testfile /tmp/test
[Task 31] [Section 5 — Advanced File Operations]: find
- How do you find files that have specific permissions?
ANS: -per* - How would you find all the files in /home
ANS: find <path> - How would you find all the files owned by paradox on the whole system
ANS: find / -user <username>
[Task 32] [Section 5: Advanced File Operations] — grep
- What flag lists line numbers for every string found?
ANS: -n - How would I search for the string boop in the file aaaa in the directory /tmp
ANS: grep boop <path>
[Task 33] Binary — Shiba3
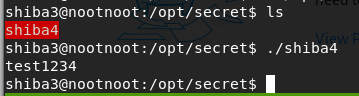
- What is shiba4’s password
find / -name shiba4 | grep shiba4 | grep shiba4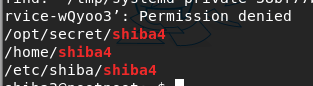
cd /opt/secret./shiba4
[Task 34] [Section 6: Miscellaneous]: Intro
su shiba4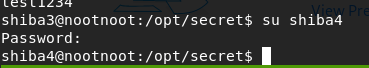
[Task 35] [Section 6: Miscellaneous]: sudo
- How do you specify which user you want to run a command as.
ANS: -u - How would I run whoami as user jen?
ANS: sudo -u jen <command> - How do you list your current sudo privileges(what commands you can run, who you can run them as etc.)
ANS: -l
[Task 36] [Section 6: Miscellaneous]: Adding users and groups
- How would I add the user test to the group test
ANS: sudo usermod -a -G <user> <group>
[Task 37] [Section 6: Miscellaneous]: nano
Let’s try open nano
nano <filename>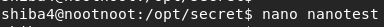
[Task 38] [Section 6: Miscellaneous]: Basic shell scripting
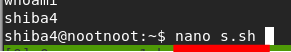
nano s.sh
In nano
echo hello
echo whoami
whoami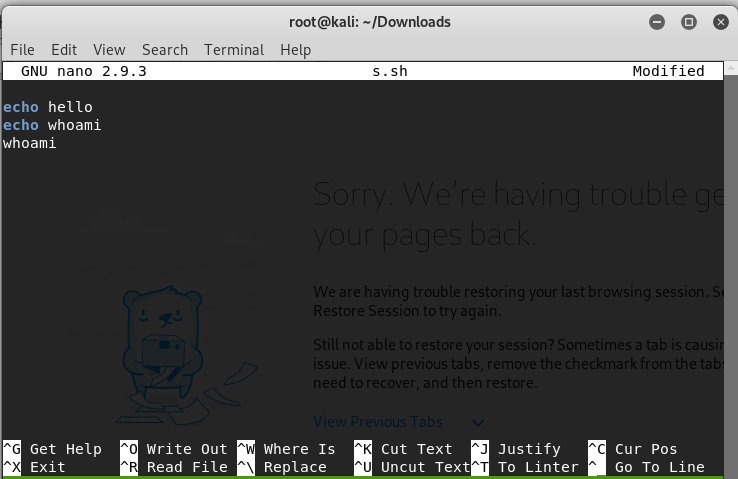
run the script
bash s.sh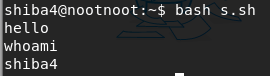
add “#!/bin/bash”
nano s.shIn nano
#!/bin/bash
echo hello
echo whoami
whoami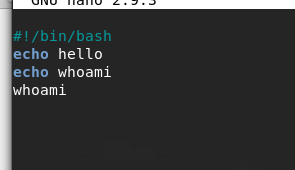
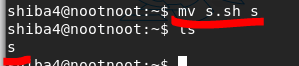
edit from s.sh to s
mv s.sh sls
edit permission
chmod 777 s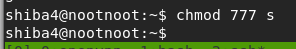
run the script
./s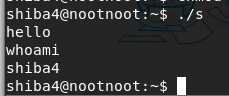
[Task 39] [Section 6: Miscellaneous]: Important Files and Directories
[Task 40] [Section 6 — Miscellaneous]: Installing packages(apt)
[Task 41] [Section 6: Miscellaneous]: Processes
List the processes
ps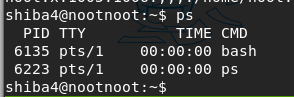
[Task 42] Fin ~
[Task 43] Bonus Challenge — The True Ending
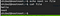
Let’s search through each user’s files.
find / -user <username> -type f 2>>/dev/null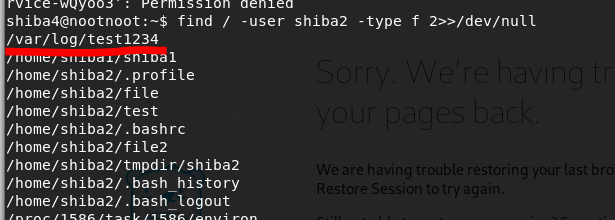
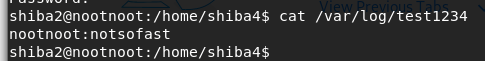
cat /var/log/test1234Permission Denied!!!
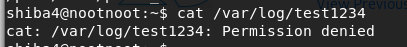
ls -l /var/log/test1234It’s belong to shiba2
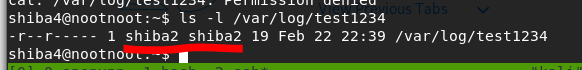
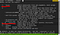
su shiba2cat /var/log/test1234
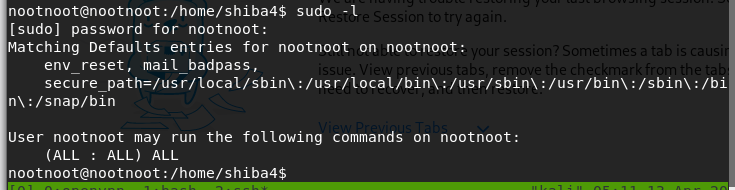
su nootnootCheck if nootnoot can run sudo
sudo -lnootnoot can run sudo command
sudo cat /root/root.txt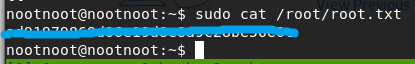












































Comments
Post a Comment